Attacks have been reported on three new victims from the well-known Nefilim crime actors. The victims in the latest round of attacks include Spirit Airlines (a $3 billion airline), Vitro (a leading glass manufacturer in North America), and Grimmway Farms (a global producer of carrots). Publication of these attacks in the past has indicated a failure to pay a ransom demand.
As of March 4, 2021, Spirit Airlines data has started to leak online, including multiple zipped archives of credit card reports.
As of March 16, 2021, Vitro files have started to leak online.
Note: We’ll be updating the post as new information becomes available such as the impact to customers, suspected size of ransom demand, and specifics of the breaches. For an example of the type of post-breach details that can come to light see our article detailing the recent Garmin breach.
If you have information about the recent Nefilim attacks or any other unreported cyber attacks, contact us at: [email protected].
Who is Nefilim?
Nefilim (or Nephilim) is ransomware used by crime actors commonly referred to by the same name. It became active in February 2020. Nefilim is similar to Nemty (another popular ransomware) in its code, but lacks the Ransomware-as-a-Service aspect. It also differs on preferred ransom payment—focusing on email communication instead of a Tor website for payment. Currently, Nefilim appears to be fairly secure, giving victims no real route to recover files without paying the ransom.
Active for just over a year, the Nefilim group has attacked several high-profile victims including the Toll Group, Orange S.A., Dussmann Group, and Luxottica. Perhaps one of the most well-known Nefilim attacks was Whirlpool in December of 2020. Stolen files were published online—documents included employee benefit information, medical requests, background checks, and accommodation requests.
Nefilim, among an increasing number of other ransomware gangs, is known for leaking stolen information if a ransom demand isn’t paid.
What is Nefilim’s process?
For most victims, the Nefilim group exploits vulnerabilities in Citrix software. Other cases have used compromised credentials and Remote Desktop Protocol (RDP) access. Administrative access is gained through privilege escalation, once the crime actors get in, they can change their privileges and gain access to more secure files and systems.
A typical Nefilim attack will follow this process. First, entry into your system through a Citrix vulnerability or compromised credentials and RDP access. The crime actors can then harvest credentials using Mimikatz, explore your Active Directory with AdFind, and identify other vulnerable systems with port scanning. Second, on each device they compromise, the crime actors will find files to encrypt, steal, and/or leak.
Next, it’s time for data exfiltration. MEGAsync is used for the actual file extraction. This process can go on for weeks, even months. The longer the crime actors have inside your system, the more files they can extract. And the final step? Deploy ransomware.
For the more technical reader, it’s important to note that Nefilim uses AES-128 to encrypt files and an RSA-2048 public key to encrypt the AES key. The public key is just that—public. But the crime actors create a secret (private) key—available with ransom demand payment—to decrypt the data.
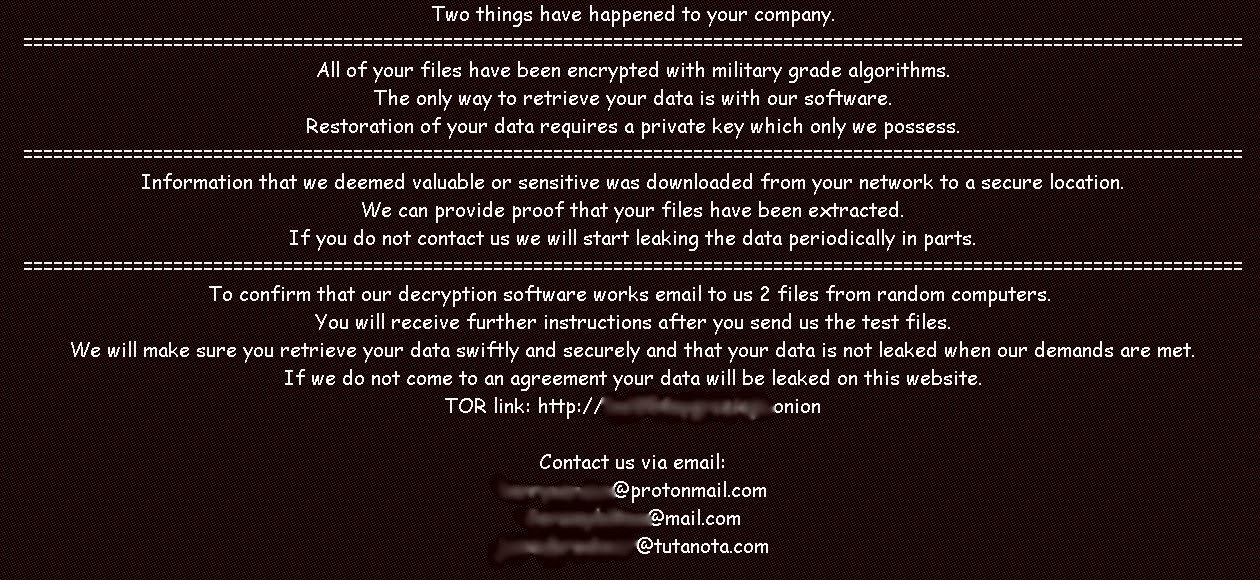
Here’s an example of a ransomware message after data has been encrypted:
How do we know about these attacks?
Measured continuously monitors the threat landscape and active attacks to keep our customers safer and assess portfolio wide risk.This system allows us to notify customers of specific phishing attacks, software, and hardware vulnerabilities and provides actionable steps to protect their infrastructure while keeping tabs on firmographic trends in malware targets.
The victims in the recent Nefilim attacks are not Measured clients.
Protect yourself from cyber attacks
To protect yourself in today’s cyber security landscape, a well-trained and well-funded internal team or external partner is critical. Experienced teams understand how to mitigate risk, execute response plans after an attack, and assess total damage in all areas of the business. In the case of the recent Nefilim attacks, a few well-known security measures might have helped:
- Disabling or cautiously handling remote access systems, such as Citrix and Remote Desktop Protocol
- Ensuring Citrix software is up-to-date
- Enabling 2-factor authentication for all accounts, at every privilege level
- Reviewing firewall rules, privileged accounts, network detection, Incident Response (IR) plan, and Endpoint Detection and Response (EDR) capabilities
- Tracking large data out-flows which might indicate data exfiltration
No security plan can be executed perfectly, nor can it predict every attack (learn more about all of the different types of ransomware attack examples in our post on the subject). To mitigate your risk further, make sure you have the right cyber insurance coverage. General insurance policies are not built to cover every impacted area of the business after a cyber attack. Most modern cyber insurance policies include broad coverage.
You don’t just need cyber insurance, you need a cyber security partner. In these recent Nefilim attacks, the right cyber insurance policy and partner would provide 24/7 experts at the first detection of the breach or ransom demand, ongoing remediation until the ransom event is resolved, and post-breach services to make sure all systems are clean of malware, preventing subsequent attacks.
If you have information about the recent Nefilim attacks or any other unreported cyber attacks, contact us at: [email protected].


 (
(