At Measured Analytics and Insurance, we aim to mitigate cyber risk with technology and education. On a continuous basis, we scan the internet for infrastructure assets that are vulnerable to various cyber security threats.
After the F5 BIG-IP vulnerability was first released, we quickly developed a detection capability based on the new vulnerability. We have run the new scanner on all Measured cyber security insurance policyholders.
See below for more information on F5’s vulnerability alerts and recommendations.
–
F5 has disclosed CVE-2022-1388, a critical vulnerability with a severity rating of 9.8. Through the management port and/or self IP addresses, an attacker with network access to the BIG-IP system can potentially execute arbitrary system commands, create or delete files or disable services. An entire device can be taken over if successful.
There is a greater risk of this vulnerability in networks that do not enforce access rules or do not segment data properly. Inadvertently, this could cause internal resources to be exposed.
According to Shodan, there were more than 19,000 potentially vulnerable devices that were accessible and internet-facing at the time the check took place, as shown in Figure 2, and Figure 1, which illustrates more than 3,000 potentially vulnerable devices in the United States.
Figure 1 – Shodan results showing the number of exposed F5 BIG-IP interfaces by country (Source: Shodan)
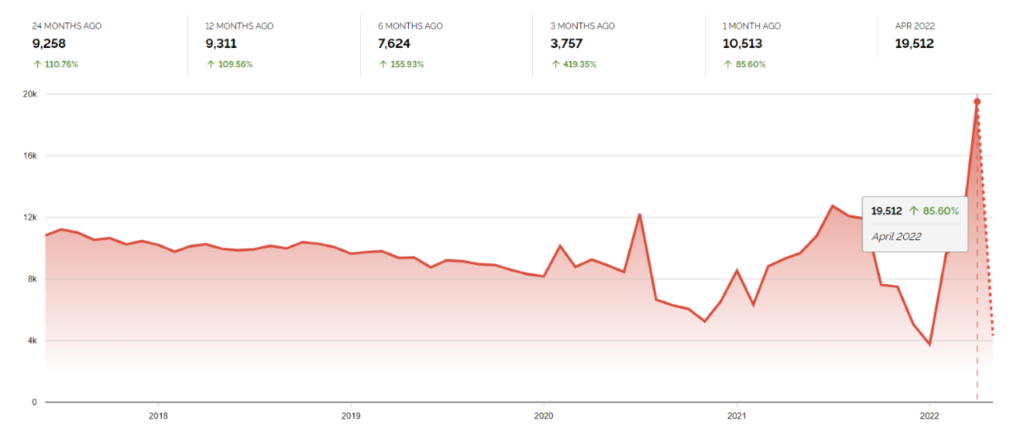
Figure 2 – Shodan results showing the number of exposed F5 BIG-IP interfaces (Source: Shodan)
F5 announced on March 10, 2021, a similar vulnerability that affected the iControl REST endpoint (CVE-2021-22986). Within days of this announcement, Measured observed exploitation and attacks begin against vulnerable devices.
Potential Mitigations
For those unable to install a fixed version immediately, F5 recommends three temporary mitigations. These mitigations restrict access to iControl REST to only trusted networks or devices, thereby limiting the attack surface.
· Block iControl REST access through the self IP address
· Block iControl REST access through the management interface
· Modify the BIG-IP httpd configuration
Exploitation May Soon Begin
As of May 5, no exploits are known to exist for this vulnerability. Measured estimates that exploitation will begin soon, though, due to a large number of easily identifiable exposed systems online. Due to the way this vulnerability lends itself to common TTPs of ransomware attacks, it is highly likely that cybercriminals will try to exploit it.
Recommendations
Measured recommends installing the latest BIG-IP version as soon as possible, as it includes crucial patches and security updates. In addition, Measured recommends limiting the exposure of all management interfaces to the internet.
References:
· F5 Advisory on CVE-2022-1388: https://support.f5.com/csp/article/K23605346
· F5 Advisory on CVE-2021-22986: https://support.f5.com/csp/article/K03009991
· CISA Alert: https://www.cisa.gov/uscert/ncas/current-activity/2022/05/04/f5-releases-security-advisories-addressing-multiple
· Bad Packets Tweet: https://twitter.com/bad_packets/status/1372650076024107009?ref_src=twsrc%5Etfw
· Shodan: https://www.shodan.io/search?query=http.title%3A%22BIG-IP%26reg%3B-+Redirect%22
· Redscan Threat Intelligence Report: https://www.redscan.com/media/Redscan-Threat-Intelligence-Report-20210312.pdf
Measured is Here to Help
Measured is standing by to answer any questions you may have. You can reach us directly at [email protected]

