What is currently considered the largest ransom ever demanded and recorded by a cyber ransomware gang may be doubling to $100 million. In March 2021, reports surfaced that the REvil ransomware group breached Acer, a Taiwanese electronics and computer manufacturer with over 7,000 employees. With nearly $8 billion in revenue reported in 2019, Acer is the sixth largest PC vendor in the world.
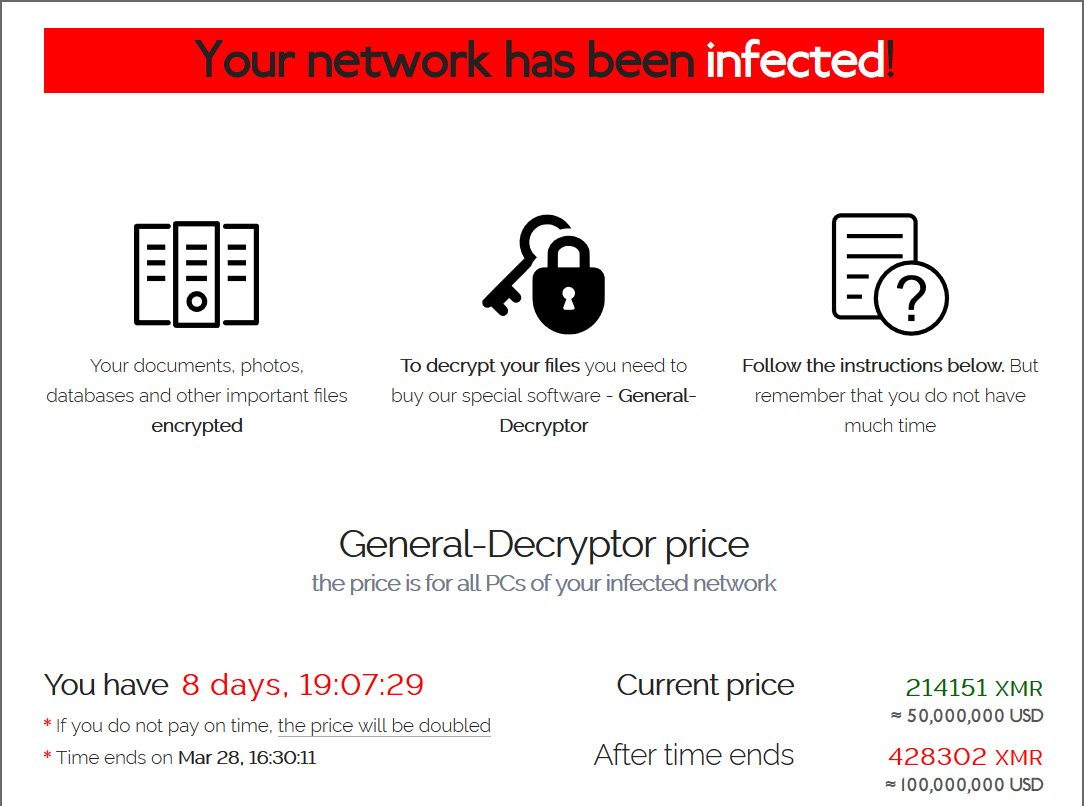
Conversations between Acer and REvil started on March 14th after stolen documents and information were leaked online. REvil publicly announced the Acer breach, claiming responsibility, while sharing financial spreadsheet images, bank messages, and bank balance information. The REvil group demanded a $50 million ransom (the largest ransom to ever be demanded to date), to be paid by March 28, 2021, threatening to double the demand if the payment was late. Among the posted instructions, the REvil group explained that upon payment, REvil would provide Acer with a vulnerability report, the decryptor to unlock their files, and REvil would delete the stolen data. The ransomware group offered a 20% discount on the $50 million demand if Acer paid by March 17, 2021. That date lapsed, as has the 28th, without any news of a payment.
Note: We’ll be updating the post as new information becomes available such as the impact to customers and specifics of the breaches. For an example of the type of post-breach details that can come to light see our article detailing the recent Garmin breach.
If you have information about the recent zero-day vulnerabilities or cyber attacks, contact us at: [email protected].
Some experts believe there is a possible connection in the breach to the Microsoft Exchange exploitation. There are reports that the REvil group targeted a Microsoft Exchange server on the Acer server this year. If the group did exploit this specific vulnerability, it would be one of the higher-profile attacks for the Microsoft Exchange vulnerability and likely a first for one of the larger ransomware groups to use this specific attack vector.
While Acer has not publicly confirmed a ransomware attack from REvil, they have stated that they’ve experienced some abnormalities recently.
“Acer routinely monitors its IT systems, and most cyberattacks are well defensed. Companies like us are constantly under attack, and we have reported recent abnormal situations observed to the relevant law enforcement and data protection authorities in multiple countries.”
Who is REvil?
The REvil ransomware group, also known as Sodinokibi, first appeared in 2019. The malware they utilize was acquired from another ransomware group (likely GandCrab) and modified to meet their needs. REvil is known for re-victimizing targets, releasing stolen data even after the ransom demands are met. Their name was inspired by the Resident Evil movie series and they are considered the most wide-spread ransomware threat in the world today—one out of every three ransomware attacks typically involve REvil ransomware.
Known for using the ransomware-as-a-service method, REvil likely pays their developers between 20 – 30% of the ransom demand and remaining 70 – 80% is funneled to affiliates that gain access to the victim’s network.
The largest ransom demand in history
The attack on Acer with an initial demand of $50 million tops the previously tied record for a ransom demand from Manheim Auctions in February of 2020 for $30 million and more recently from Dairy Farm in January of 2021 for $30 million. The attack on the pan-Asian retail chain operator was credited to REvil. Stolen files and images were posted online as REvil publicly claimed responsibility for the attack in January.
In the Acer attack, criminal actors follow the same protocol, posting images and information online. In the following image, we can see the alleged ransom note left to Acer, including a threat that the ransom will double if not paid on time. The date to pay the $50 million has passed. If the criminal actors adhere to their word on this note, the new ransom is $100 million.
How are ransomware attacks evolving?
Ransomware attacks, like the one on Acer, are evolving beyond that traditional ransomware attack to focus on extortion. Criminal actors are forgoing the groundwork of installing malware and instead, they are targeting vulnerabilities and systems that enable them to get access to highly sensitive data and then extort their victims.
This is an escalation of efforts for criminal actors. And while it’s certainly more work for their teams upfront, it can offer a higher ROI if businesses pay out. Exploiting vulnerabilities like Accellion FTA or Microsoft Exchange allows ransomware groups to skip the pre-work of initial access with phishing emails, using a tool to escalate privileges (based on who clicked on a phishing email), mapping the enterprise, finding sensitive data to steal, and then stealing that data for ransom or extortion.
A direct attack on a system through a vulnerability saves the criminal actors time, allowing them to target high profile companies that are impacted by zero-day vulnerabilities.
To learn more about the Microsoft Exchange zero-day vulnerability, click here.
To learn more about ransomware-as-a-service and other ransomware trends, click here.
How to protect yourself against ransomware attacks
Every ransomware attack is different, making it critical to protect yourself against as many attacks as possible. And while there’s so much you can do, there are security issues you can address in the short term to make your business safer. Here are five key steps you can take today:
1. Add email filtering. While the Acer breach likely wasn’t initiated with a phishing email, many ransomware attacks use this common attack method. In fact, in the Dairy Farm attack, REvil threatened to use their privileges to send phishing emails from Dairy Farm, targeting customers with a new, sophisticated approach to phishing emails.
By adding email filtering, you can block malicious emails before they get delivered to your system. Every email should be scanned (including attachments) both before it’s delivered and before it’s sent (in case of an attack from the inside). Malicious emails are flagged and can then be reviewed in case of a system mistake.
2. Add malicious website blocking. Another common attack method, malicious websites are the perfect inroad for criminal actors into your network and devices. With the correct blocking software, you can prevent access to known malicious sites and IP addresses, avoiding a cyber attack initiated by an unknowing employee.
3. Disable Remote Desktop Protocol (RDP). For many criminal actors, RDP offers an easy entry into your system or network. By disabling RDP unless absolutely necessary, you can prevent a large number of attacks. If it is enabled, make sure it’s properly configured and software is always up-to-date.
4. Keep your operating system and software up-to-date. While some ransomware attacks stem from unknown vulnerabilities, many criminal actors exploit well-known vulnerabilities in operating systems and software. Require that all updates for all systems are consistently updated. These critical updates include patches for known security holes and can close an otherwise open door to attackers.
5. Understand your current cyber risk. Assessing your cyber risk is another critical step in preventing a cyber attack. With the right cyber risk management partner, you can get a complete report of current vulnerabilities and a list of actions to shore up your network and business against an attack from criminal actors.
While no one can predict every possible cyber attack, these practices can reduce your overall risk. With the right cyber insurance partner, you can assess your current risk, fix existing vulnerabilities, and prepare your business with the right coverage for every area of impact.
If you have information about the recent Exchange zero-day vulnerabilities or consequential attacks, contact us at [email protected].
To check your current risk and learn more about the recommended coverage for a cyber attack, check out our risk calculator here.