Over 3 billion domain spoofing emails are sent every day with the average social engineering attack scamming victims out of $75,000. Nearly 30,000 spoofing attacks are reported each day and the number is expected to rise. Domain spoofing, a common phishing technique, continues to be a common cyber threat.
Read on to learn more about domain spoofing, how domain spoofing works, and how to avoid domain spoofing.
This article is part of our Definitive Guide to Phishing series:
WHAT IS DOMAIN SPOOFING?
Domain spoofing is a type of social engineering, often categorized under phishing. A third-party will replicate a reputable business website and use it to trick new visitors into entering sensitive information (credit card number, personal data, etc.).
HOW DOES DOMAIN SPOOFING WORK?
Domain spoofing can target employees or customers and the new site is usually sent to victims via email—though fake sites can appear in search results online as well. At first glance, the website appears legitimate and only after a more careful review can you find a few altered words or characters.
The domain spoof usually showcases the same logo as the business it’s impersonating, similar branding, and the design of the site will look like a near replica of the real site. New visitors to the fake domain will follow their usual routine and enter financial information or other sensitive data into the displayed forms. The crime actors will then steal this information and use it to their advantage.
Fake websites are typically embedded within phishing emails, enticing users to click on the link, visit the fake website, and enter sensitive information that can then be stolen and/or sold by the crime actor.
DOMAIN SPOOF EXAMPLES
There are several telling characteristics of a domain spoof. A cloned bank website is a great example. While the URL may look the same, it will usually include additional terms that may or may not be considered legitimate add-ons to the trusted URL.
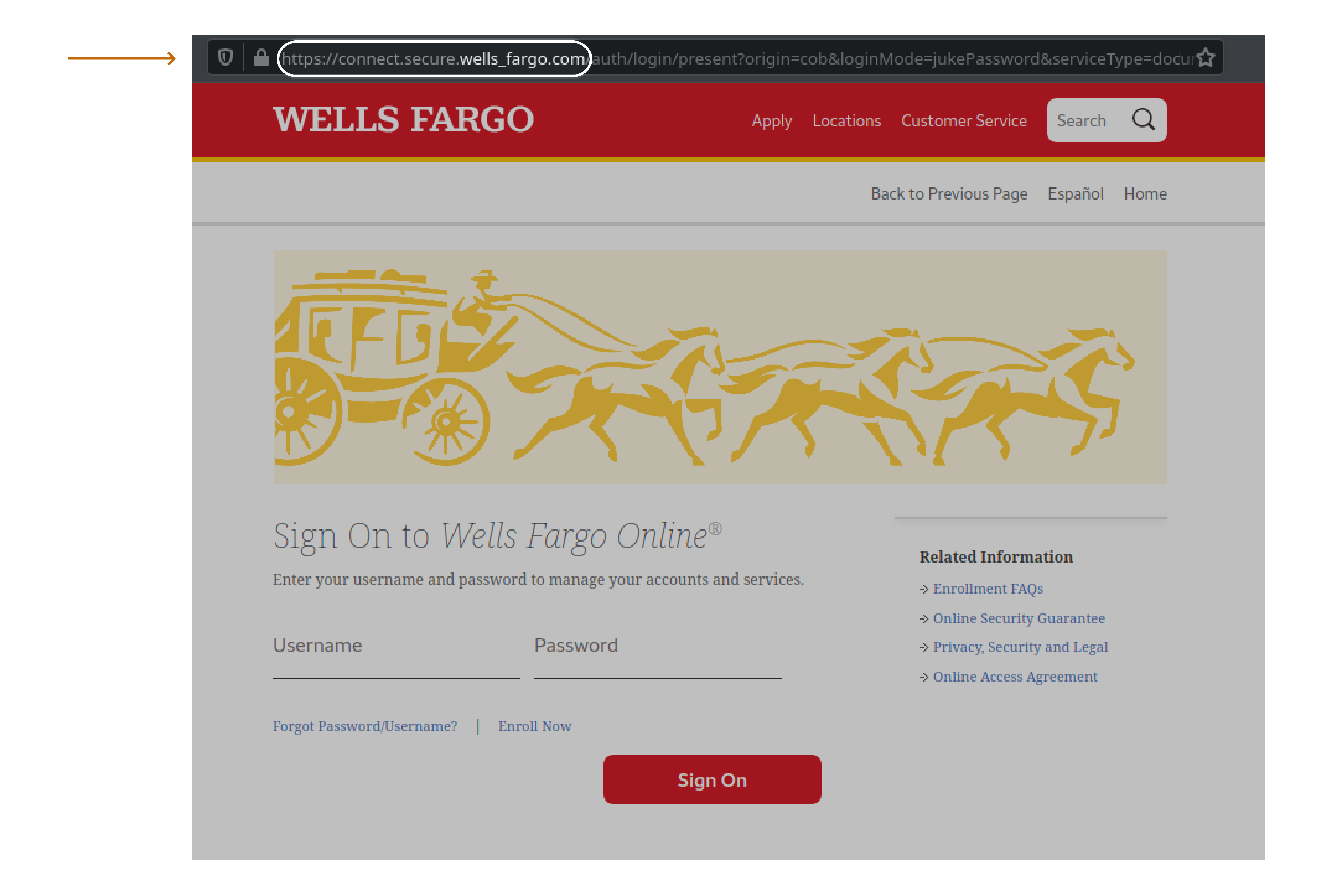
In this image you can see that the Wells Fargo website has been cloned and looks very similar, nearly identical, to the real site. But if you look at the URL you can see that the domain is actually connect.secure.wells_fargo.com. This is not the proper URL for the Wells Fargo sign in page. It is a fake website.
Before a victim visits a fake website, they’re typically targeted with a phishing email. And the email usually appears to be from a trusted source, linking to a trusted site. The sender name may be misspelled slightly or the URL may have just one or two differing characteristics from the trusted URL. Here are a few examples of URLs that could be embedded in a phishing email:
- http://example.login.com appears to be hosted by example.com but is actually hosted by login.com
- http://exampel.com just has a slight misspelling and at a quick glance looks like example.com
- http://emämple.com is an example of a homograph attack using international characters which either look similar or identical to the original character
In a recent case the fake website privnotes.com even appeared in the google search results in the number one spot (via an ad) as well as the number three result, under the legitimate site, highlighting the need to be very careful when clicking search results to important websites.
HOW TO AVOID FALLING FOR A DOMAIN SPOOF
There are several ways you can avoid falling for a domain spoof attack:
- Make sure that emails are properly filtered to reduce your chances of a phishing email
- Review sender information on every email to make sure it is from a legitimate and trusted source
- Avoid clicking directly on links that are embedded in emails (but when you do, ensure the email is truly from a trusted source)
- Double check every URL in your browser to make sure it is correctly spelled and there are no additional add-ons
- Look for anything unfamiliar in the URL name, such as a number, a misspelling, an underscore, etc.
- Review the design and placement of familiar elements on each webpage—does anything seem out of place or different? Check the URL and back out of the site before entering any sensitive information
- Bookmark legitimate sites that you frequent and often use to enter sensitive information
To learn more about the effects of phishing, such as ransomware, check out our Definitive Guide to Ransomware.

