Did you know that 95% of all malware is delivered via email? And 32% of data breaches also involve phishing. Phishing is a growing threat to businesses and individuals globally. If you’re just learning about phishing, or trying to gather information to help you combat it in your organization, we’ve compiled a guide to get you up-to-speed.
This article is part of our Definitive Guide to Phishing series:
In this post, we’ll cover:
- What is phishing?
- What is vishing?
- What is spear phishing?
- What is whaling?
- What can you do to prevent phishing?
- Phishing scams and attack examples
WHAT IS PHISHING?
To understand phishing, it’s also helpful to understand the definition of social engineering: manipulating users into performing actions against their interests such as divulging sensitive information.
Phishing, a type of social engineering, is when a third party attempts to obtain sensitive information via fraudulent electronic communication, historically email or text, but it could also include any communication such as WhatsApp, Instagram Messaging etc.
Sensitive information examples:
- Usernames
- Passwords
- Credit Card Information
These communication attempts will appear to come from a legitimate source, such as a company you trust (your bank, etc), or even a person you trust or know personally. The goal of the attack? For you to take action that will compromise your data. The action could be to download a malicious attachment (possibly installing malware, such as ransomware, on your system), click a link and then subsequently enter information on a malicious website, or in some cases, dial a number for a bank or person (which appears correct or legitimate) and relay account information to a malicious listener.
A phishing email may also appear to link to a trusted website. And there are many techniques that make it easy for a crime actor to make a fake website look legitimate. They could simply misspell the name of the bank, making it hard to detect with a quick eye scan. Or they could use the name of your bank and add to the URL. Here are a few examples to illustrate the point:
- http://example.login.com appears to be hosted by example.com but is actually hosted by login.com
- http://exampel.com just has a slight misspelling and at a quick glance looks like example.com
- http://exämple.com is an example of a homograph attack using international characters which either look similar or identical to the original character
In both scenarios–a phishing email or a phishing website–they try to match the expected look and feel of the legimitage brand they are impersonating.
WHAT IS VISHING?
Vishing, or voice phishing, is a variant of phishing. The criminal actors use voice and the phone to obtain sensitive information. It’s a similar style–they impersonate someone from a legitimate company and request information, such as your bank account number or PIN, etc.
WHAT IS SPEAR PHISHING?
Spear phishing is a type of phishing attack that targets individuals instead of sending the same email or URL to a broader group of people. The attacker will send emails from a known or trusted source (impersonating the source) with the goal of collecting information or data from a targeted recipient.
WHAT IS WHALING?
Whaling, which can also be referred to as whaling phishing, is a type of phishing attack. The target is generally high-profile employees within an organization like the CEO or CFO. The goal of a whaling attack is to steal sensitive information or to socially engineer employees to transfer funds to the criminal actor(s). In some scenarios, the attacker will impersonate the high-profile employee, the CEO or CFO, and convince an employee to complete a task, such as transferring funds or relaying sensitive information to the criminal actor.
WHAT CAN YOU DO TO PREVENT PHISHING?
While phishing in its various forms is becoming more and more prevalent, there are several actions you can take to prevent a serious phishing attack at your organization. We recommend the following:
Use an email gateway. With an email gateway, you can filter out malicious emails before they enter your inbox. Stopping the malicious email before it hits your inbox, or your employees’ inboxes, reduces the risk of you falling for any of the social engineering tactics criminal actors use in phishing attempts.
Train users to spot phishing attacks. Update your employee education to include training and examples on how to spot phishing attacks. Teach your employees to be cautious about clicking links and downloading attachments.
Manually navigate to websites and logins. Instead of relying on URLs inside emails, manually navigate to the desired website by typing in the exact URL. Using bookmarks can be another safe option to reduce the risk of clicking on a phishing email.
Never give information away on an incoming call. In the case of vishing, always call a verified number back instead of relaying account information or other data over the phone to an incoming call.
Require MFA (multi-factor authentication). Require multi-factor authentication, granting access to information after two or more pieces of evidence to an authentication mechanism are presented.
Perform timely software updates. Software updates are critical in keeping phishing attacks at bay. Updates will patch vulnerabilities in your software, including email filtering systems.
Back up data frequently and regularly. In the case of a phishing attack, especially one that results in a ransomware event, data that is backed up frequently and regularly can help you avoid paying a ransom.
PHISHING SCAMS AND ATTACK EXAMPLES
The following images showcase several phishing attack techniques.
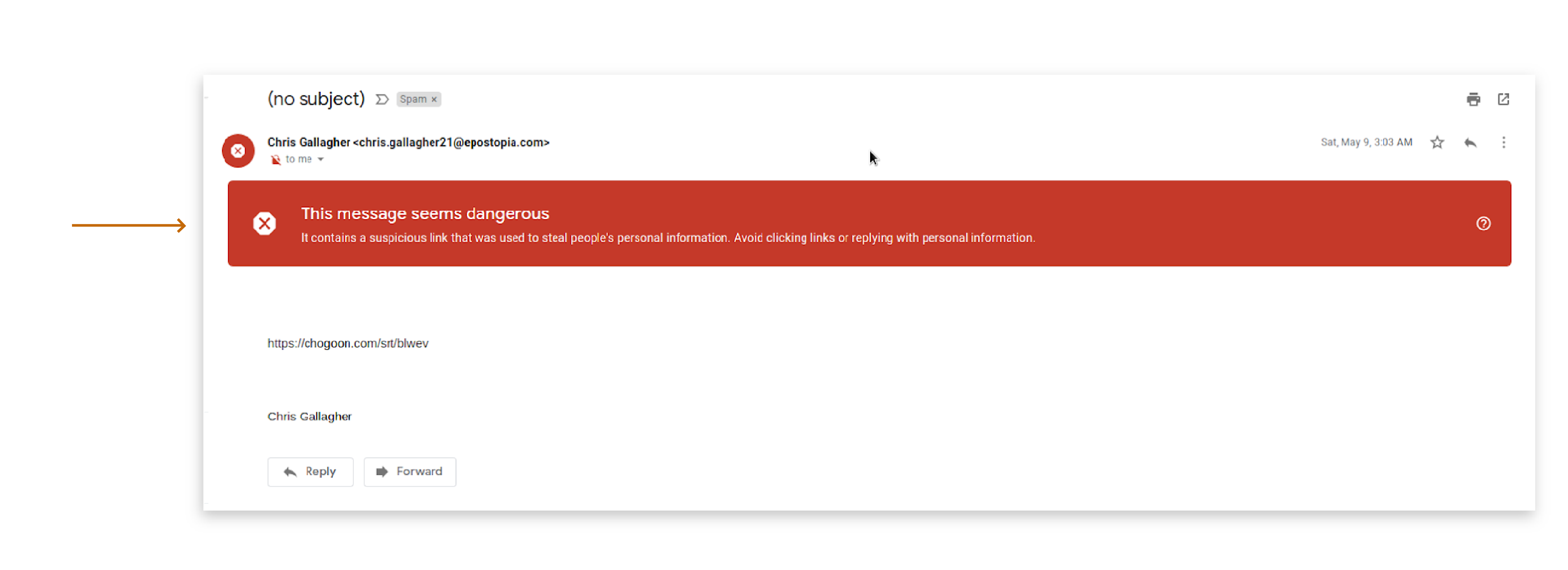
1. Obvious Phishing Email The first image is an example of spam you might be used to seeing, it has been clearly marked as such, but beware many phishing emails (especially hand crafted spear phishing emails) will not be this easy to spot:
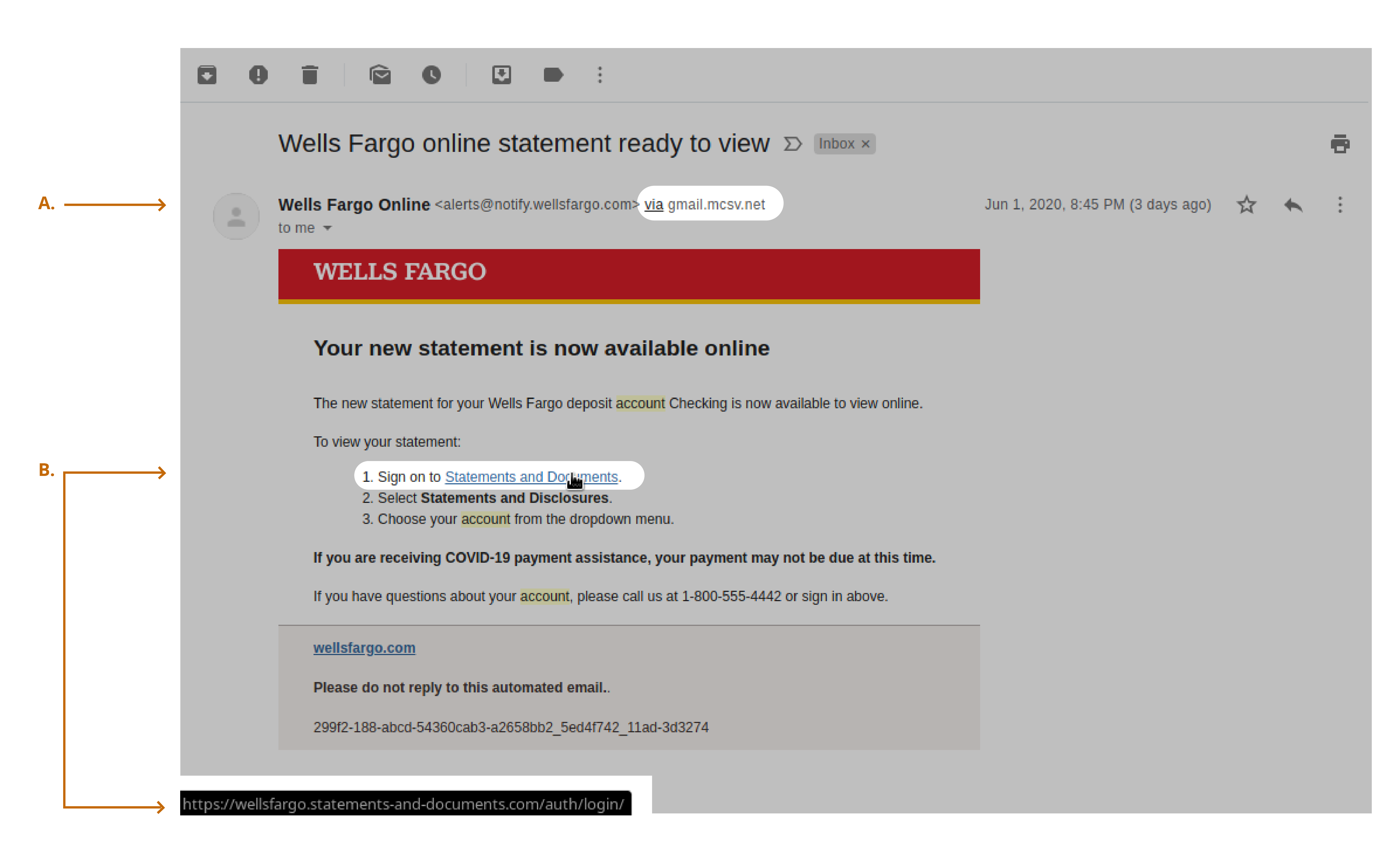
2. Fraudulent Emails and Links In this second example, the email seems to be from a trusted bank. Note that the sender is the bank name, but sent “via” a gmail address (A). This is a clue that this email is not from the sender it says it is.
Another warning sign is when you hover over the suggested link for Statements and Documents (B), you can see that the URL is .statements-and-documents.com instead of the bank’s URL.
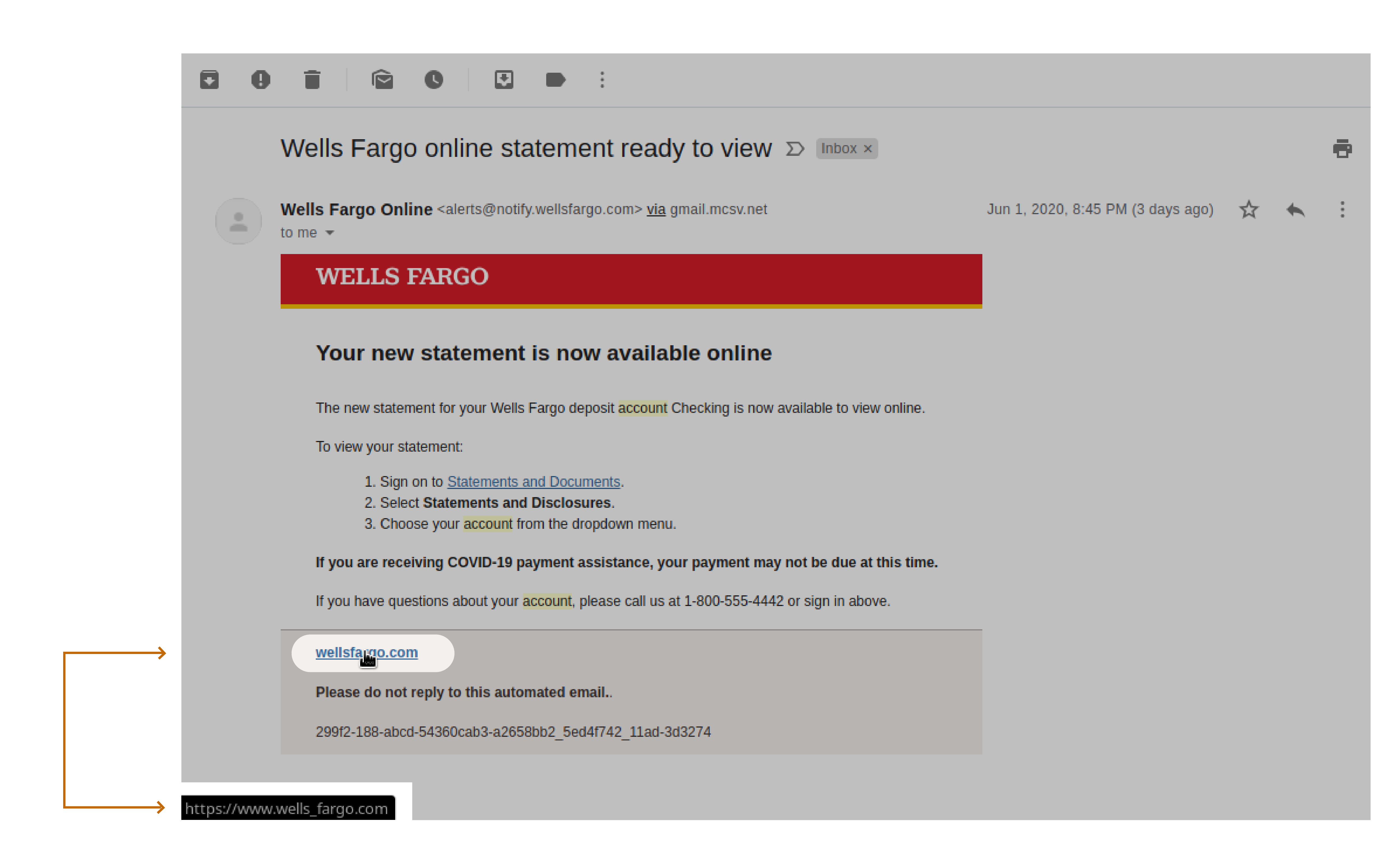
3. Fraudulent Emails and Links In this third example, you can see another URL possibility, an unusual character. In this example, the attackers have added an underscore to change the URL to wells_fargo.com:
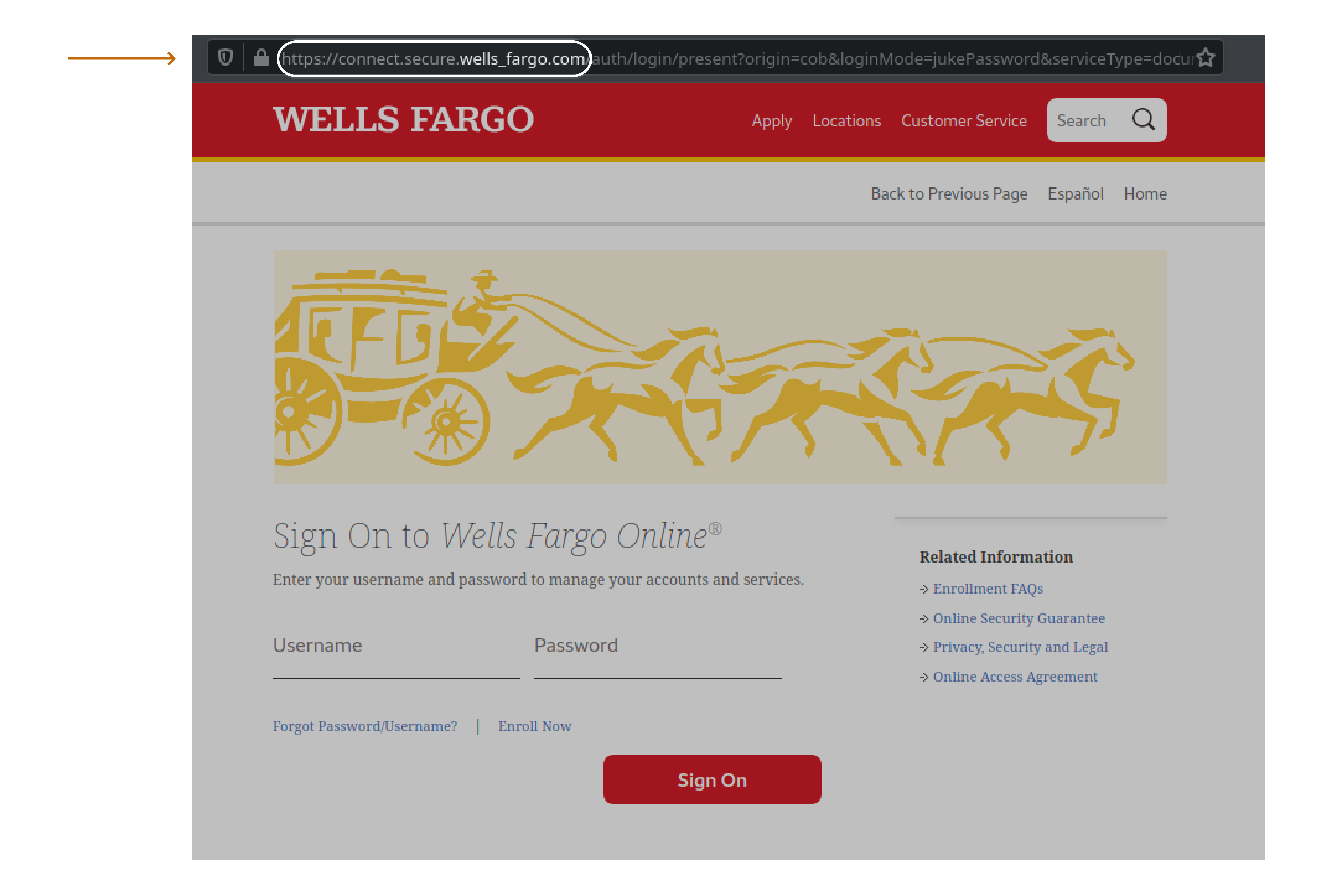
4. Cloned Websites and Incorrect URLs In the final example, you can see a cloned bank website. In the URL, note that the domain is actually connect.secure.wells_fargo.com. This is not the proper URL for the bank:
To learn more about the effects of phishing, such as ransomware, check out our Definitive Guide to Ransomware.

